Unit 42's Attribution Framework: A Scientific Approach to Threat Classification
Unit 42's Attribution Framework: A Scientific Approach to Threat Classification
In the ever-evolving world of cybersecurity, accurately identifying and classifying threat actors is crucial for effective defense. Unit 42, the threat intelligence team at Palo Alto Networks, has recently unveiled a comprehensive Attribution Framework designed to bring scientific rigor and consistency to this challenging process. This framework promises to transform threat attribution from an "art" to a more data-driven discipline.
The Challenge of Threat Attribution
Traditionally, attributing cyberattacks to specific threat actors has been a complex and often subjective endeavor. It relied heavily on the expertise of a few threat researchers, making the process inconsistent and difficult to scale. Factors such as overlapping tactics, techniques, and procedures (TTPs), as well as the use of commodity malware, further complicated the attribution process.
Introducing the Unit 42 Attribution Framework
The Unit 42 Attribution Framework provides a systematic and data-driven methodology for classifying threat actors based on their observed activities. It aims to address the long-standing challenges of inconsistent and subjective threat attribution by:
- Providing a structured approach for analyzing threat data.
- Facilitating the attribution of observed activities to formally named threat actors, temporary threat groups, or activity clusters.
- Enhancing the accuracy and reliability of threat intelligence.

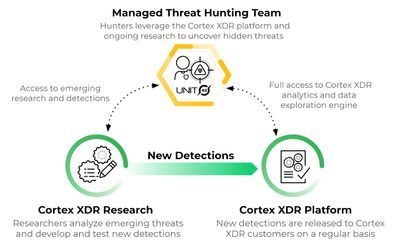
Cortex XDR Managed Threat Hunting | Palo Alto Networks
Key Components of the Framework
While the specific details of the framework are likely more extensive than publicly available, the core idea revolves around establishing a consistent and repeatable process for analyzing threat data. This likely involves:
- Collecting and analyzing relevant data points, such as malware samples, network traffic, and attacker infrastructure.
- Identifying patterns and trends in attacker behavior.
- Comparing these patterns to known threat actor profiles.
- Assigning a confidence level to the attribution based on the available evidence.
Benefits of a Scientific Approach
By adopting a more scientific approach to threat attribution, organizations can benefit in several ways:
- Improved accuracy: Data-driven attribution reduces the risk of misattribution, leading to more effective security measures.
- Enhanced efficiency: A systematic framework streamlines the attribution process, saving time and resources.
- Better collaboration: A common framework facilitates communication and collaboration among security teams and organizations.
- Proactive defense: Accurate threat attribution enables organizations to anticipate and mitigate future attacks.
Key Takeaways
The Unit 42 Attribution Framework represents a significant step forward in the field of cybersecurity. By bringing scientific rigor to threat attribution, it promises to improve the accuracy, efficiency, and effectiveness of threat intelligence, ultimately leading to a more secure digital world.