vulnerability-exploitation
Threat Actors Are Exploiting Vulnerabilities Faster: What You Need to Know
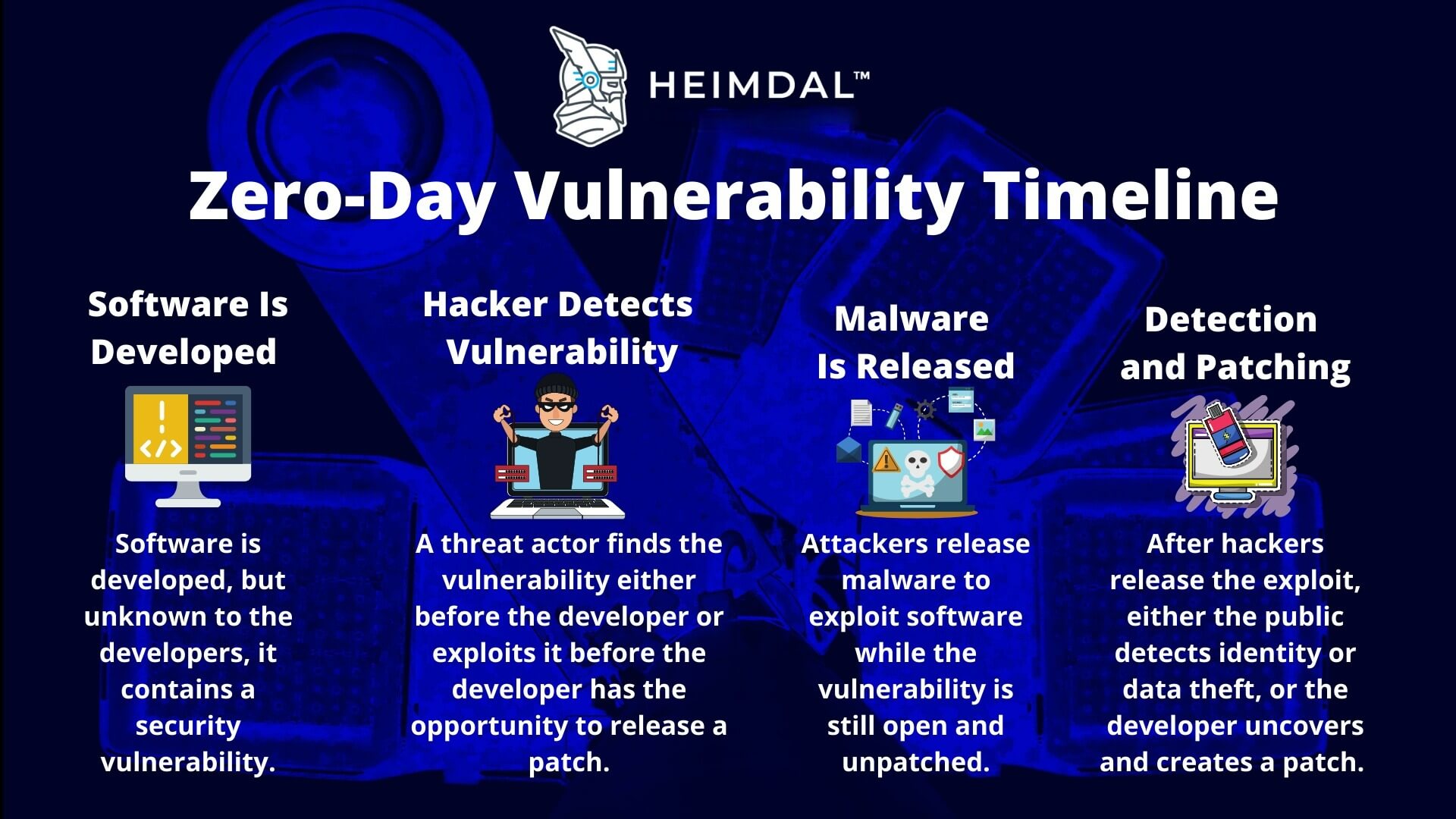
Threat Actors Are Exploiting Vulnerabilities Faster: What You Need to Know In today's rapidly evolving threat landscape, cybercriminals are becoming increasingly adept at exploiting vulnerabilities in software and systems. What was once a race against the clock measured in weeks or months has now shrunk to days, or
