rmm-tools
Silent Infiltration: How Threat Actors Abuse RMM Tools for Initial Access
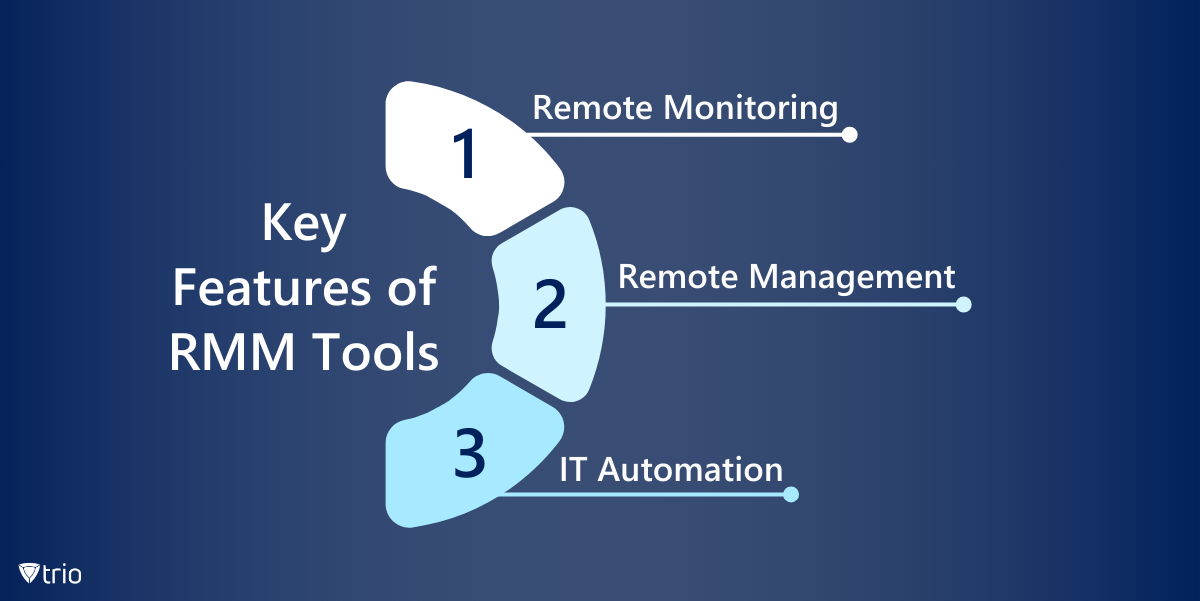
Silent Infiltration: How Threat Actors Abuse RMM Tools for Initial Access In today's evolving threat landscape, cybercriminals are constantly seeking new ways to infiltrate organizations. One increasingly popular tactic involves abusing legitimate Remote Monitoring and Management (RMM) tools. These tools, designed to help IT professionals manage and maintain
