Mustang Panda Masquerades as Chrome: Toneshell Malware Targets Windows
Mustang Panda Masquerades as Chrome: Toneshell Malware Targets Windows
A new wave of cyberattacks is targeting Windows users, with the notorious Mustang Panda APT group employing a clever disguise. This time, they're using the Toneshell malware, meticulously crafted to mimic the appearance and behavior of Google Chrome, to infiltrate systems and steal sensitive information.

Mustang Panda deploys a new wave of malware targeting Europe
Understanding the Threat: Mustang Panda and Toneshell
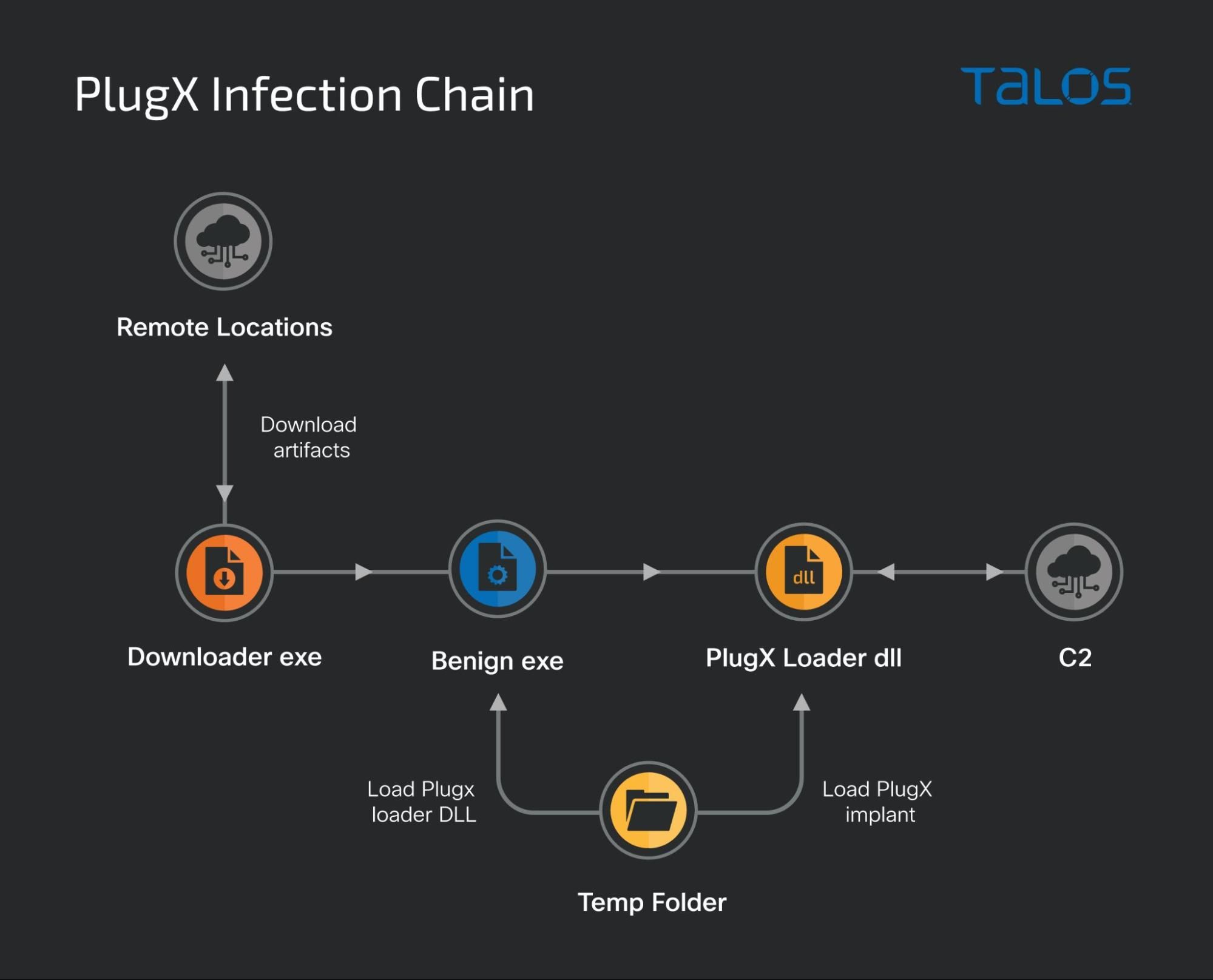
Mustang Panda, a China-linked advanced persistent threat (APT) group, has a history of targeting government, military, and other high-value sectors. They are known for their sophisticated techniques, constantly evolving their methods to evade detection and maximize impact. Toneshell is a backdoor malware used by Mustang Panda to gain unauthorized access to compromised systems. It allows them to execute commands, steal data, and deploy additional malicious payloads.
The Chrome Disguise: How the Attack Works
In this latest campaign, Mustang Panda is distributing Toneshell disguised as a legitimate Google Chrome installer or update. This social engineering tactic relies on tricking users into downloading and executing the malicious file. Once executed, Toneshell installs itself on the system and establishes a connection with the attacker's command-and-control (C2) server. The malware can then perform various malicious activities, including:
- Data exfiltration: Stealing sensitive documents, credentials, and other valuable information.
- Remote control: Allowing the attackers to remotely control the compromised system.
- Lateral movement: Spreading the malware to other systems on the network.
- EDR Evasion: Bypassing security measures like Windows Defender and Kaspersky.
防禦措施: Protecting Yourself from Mustang Panda
Protecting yourself from sophisticated threats like Mustang Panda requires a multi-layered approach:
- Be cautious of suspicious emails and websites: Avoid downloading files or clicking on links from unknown or untrusted sources.
- Keep your software up to date: Regularly update your operating system, web browser, and other software to patch security vulnerabilities.
- Use a reputable antivirus solution: Install and maintain a reliable antivirus program with real-time scanning capabilities.
- Implement strong password policies: Use strong, unique passwords for all your accounts and enable multi-factor authentication where possible.
- Educate yourself and your employees: Train users to recognize phishing attempts and other social engineering tactics.
Key Takeaways
Mustang Panda's use of Toneshell malware disguised as Google Chrome highlights the importance of vigilance and a proactive security posture. By understanding the tactics used by these threat actors and implementing appropriate security measures, you can significantly reduce your risk of falling victim to their attacks.
References
- The Hacker News - Mustang Panda Targets Myanmar With StarProxy, EDR Bypass, and TONESHELL Updates
- The Hacker News - Camaro Dragon Hackers Strike with USB-Driven Self-Propagating Malware
- Bleeping Computer - Chinese hackers abuse Microsoft APP-v tool to evade antivirus
- Security Online - Mustang Panda Backdoor Exposed: New ToneShell Malware ...
- Talos Intelligence - Mustang Panda Image





