Linux Servers Under Siege: Defending Against Undetectable SSH Attacks
Linux Servers Under Siege: Defending Against Undetectable SSH Attacks
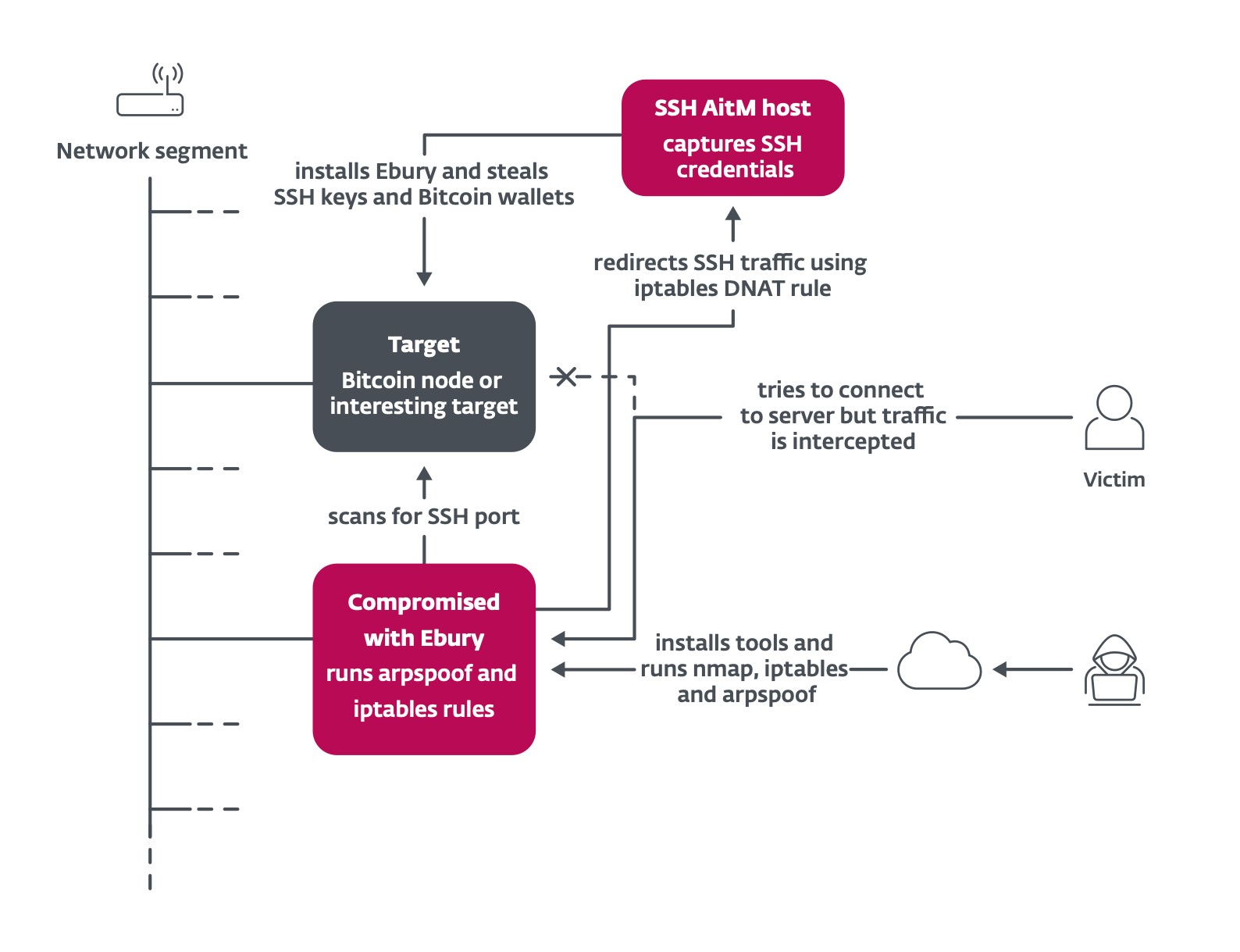
Linux servers are the backbone of countless applications and services, making them prime targets for malicious actors. A new wave of attacks, often dubbed "undetectable plague" due to its stealthy nature, is targeting Linux servers to gain persistent SSH access. This article will delve into the techniques used in these attacks and provide actionable steps to protect your systems.

Ebury is alive but unseen: 400k Linux servers compromised for ...
Understanding the Threat
The core of this attack involves compromising the Secure Shell (SSH) service, the primary method for remote server administration. Attackers are employing sophisticated methods to bypass traditional security measures and maintain long-term access to compromised systems. The primary attack vectors include:
- Trojanized OpenSSH Binaries: Attackers replace legitimate OpenSSH binaries with modified versions that contain backdoors. These backdoors allow them to bypass authentication and gain unauthorized access.
- Backdoor Shell Scripts: Malicious scripts are deployed to create hidden access points. These scripts often modify system files and create new user accounts with SSH access.
- Authorized Keys Modification: The
authorized_keysfile, which stores public keys for passwordless SSH login, is manipulated to add attacker-controlled keys. This grants persistent access even if the original account passwords are changed.
How the Attack Works
The attack typically unfolds in the following stages:
- Initial Compromise: Attackers gain initial access through vulnerabilities in other services or weak SSH passwords.
- Malware Deployment: Once inside, they deploy the trojanized OpenSSH binary and/or backdoor shell script.
- Persistence Establishment: The malware modifies the
authorized_keysfile, adding the attacker's public key. - Lateral Movement: With persistent SSH access, attackers can move laterally within the network, compromising other systems.
- Data Exfiltration and Malicious Activity: Finally, the attackers can steal sensitive data, install ransomware, or use the compromised server for other malicious purposes.
Protecting Your Linux Servers
Preventing these attacks requires a multi-layered security approach:
- Regularly Update Software: Keep your operating system and all installed software up to date with the latest security patches.
- Use Strong Passwords: Enforce strong password policies and consider using multi-factor authentication (MFA) for SSH access.
- Monitor SSH Activity: Implement tools to monitor SSH login attempts, unusual activity, and modifications to the
authorized_keysfile. - Implement Intrusion Detection Systems (IDS): Use an IDS to detect malicious activity on your servers.
- Regularly Audit System Files: Periodically check the integrity of system binaries, including OpenSSH, and look for unauthorized modifications. Tools like
aidecan help with this. - Disable Root Login: Disable direct root login over SSH and use
sudofor administrative tasks. - Limit SSH Access: Restrict SSH access to specific IP addresses or networks using firewall rules.
- Use Key-Based Authentication: Enforce key-based authentication and disable password authentication altogether.
Key Takeaways
The "undetectable plague" malware highlights the importance of proactive security measures for Linux servers. By understanding the attack vectors and implementing the recommended security practices, you can significantly reduce your risk of compromise and protect your valuable data.




.jpg)