EDR-on-EDR Violence: Hackers Weaponizing Free Trials to Disable Security
EDR-on-EDR Violence: Hackers Weaponizing Free Trials to Disable Security
A disturbing trend has emerged in the cybersecurity landscape: hackers are now exploiting free trials of Endpoint Detection and Response (EDR) solutions to disable existing EDR protections on target systems. This "EDR-on-EDR violence," as some researchers call it, allows attackers to bypass security measures and potentially deploy malware or carry out other malicious activities with ease.

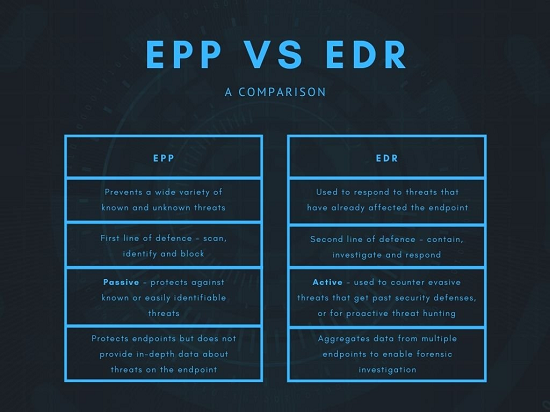
EDR Comparison | EPP vs EDR vs XDR Know Business Benefit
Understanding the "BYOEDR" Technique
This attack vector, sometimes referred to as "BYOEDR" (Bring Your Own EDR), involves attackers signing up for free trials of legitimate EDR products. Once they have access to the EDR software, they use its capabilities to identify and disable competing EDR solutions already installed on the target system. This can be achieved by manipulating system configurations, terminating processes, or uninstalling the existing security software.
The concerning aspect of this technique is that it leverages legitimate tools and functionalities, making it harder to detect and prevent. Traditional security measures may not recognize the activity as malicious because it originates from a trusted source – the EDR software itself.
The Impact on Organizations
The consequences of a successful "EDR-on-EDR" attack can be severe. By disabling existing EDR protections, attackers gain a significant advantage, allowing them to:
- Deploy ransomware and encrypt critical data.
- Steal sensitive information, such as customer data or intellectual property.
- Gain persistent access to the network for future attacks.
- Disrupt business operations and cause financial losses.
This type of attack is particularly dangerous because it targets a fundamental layer of security, leaving organizations vulnerable to a wide range of threats.
How to Protect Your Organization
While the "EDR-on-EDR" attack is sophisticated, there are steps organizations can take to mitigate the risk:
- Implement strong access controls: Restrict access to EDR management consoles and limit the privileges of user accounts.
- Monitor EDR activity: Continuously monitor EDR logs and alerts for suspicious activity, such as unauthorized software installations or configuration changes.
- Employ application control: Use application control solutions to restrict the execution of unauthorized software, including potentially malicious EDR agents.
- Harden endpoint configurations: Implement security best practices to harden endpoint configurations and prevent unauthorized modifications.
- Regularly review security posture: Conduct regular security assessments and penetration tests to identify vulnerabilities and weaknesses in your security defenses.
- Consider XDR solutions: Extended Detection and Response (XDR) solutions provide a more holistic approach to security by integrating data from multiple sources, offering better visibility and threat detection capabilities.
Key Takeaways
The weaponization of free EDR trials is a serious threat that organizations need to be aware of. By understanding the "BYOEDR" technique and implementing appropriate security measures, you can significantly reduce your risk of falling victim to this type of attack. Staying proactive and continuously monitoring your security posture is crucial in today's evolving threat landscape.
References
- https://www.xcitium.com/images/edr-comparison.png
- https://www.csoonline.com/article/4032009/edr-on-edr-violence-hackers-turn-security-tools-against-each-other.html
- https://threatnote.com/infosec-news/from-cyber-security-news-hackers-weaponizing-free-trials-of-edr-to-disable-existing-edr-protections/
- https://gbhackers.com/hackers-abuse-edr-free-trials/