Critical Alert: SonicWall VPN Zero-Day Exploited to Bypass MFA, Deploy Ransomware
Critical Alert: SonicWall VPN Zero-Day Exploited to Bypass MFA, Deploy Ransomware
A serious security threat is unfolding as SonicWall VPNs are being actively exploited through a likely zero-day vulnerability. This flaw allows attackers to bypass multi-factor authentication (MFA) and deploy ransomware, with the Akira ransomware group being a prominent actor. Organizations using SonicWall VPNs are urged to take immediate action to mitigate this risk.

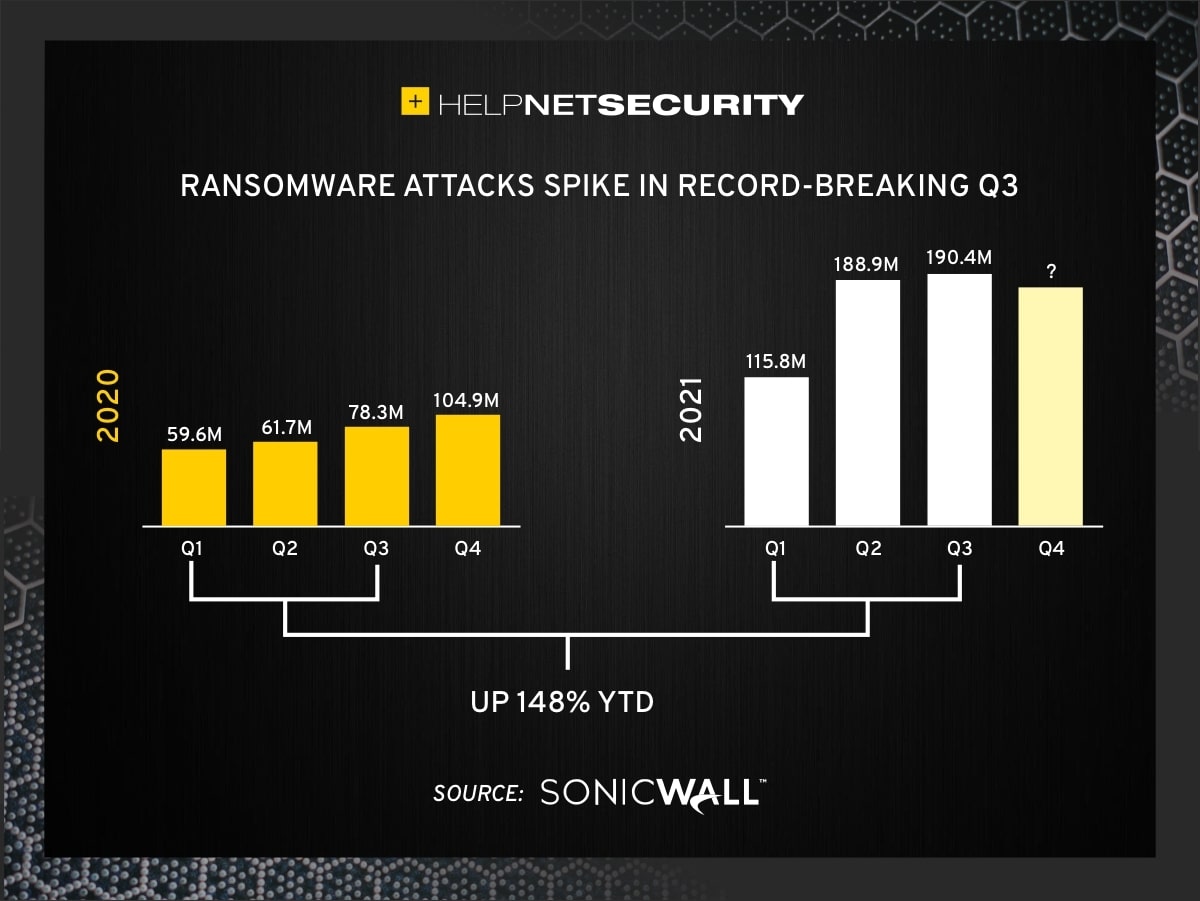
50+ Ransomware Statistics & Facts for 2018-2022
The Threat: Zero-Day Exploitation and MFA Bypass
Recent reports indicate that a zero-day vulnerability is being exploited in SonicWall SSL VPN products. This vulnerability allows attackers to gain unauthorized access to corporate networks, even when MFA is enabled. The attackers are then able to move laterally within the network and deploy ransomware.
- Attackers are bypassing MFA, indicating a sophisticated exploit.
- Compromised VPN access is leading to rapid ransomware deployment.
- Fully patched devices are still vulnerable, suggesting a zero-day.
Akira Ransomware: A Key Player
The Akira ransomware group is actively exploiting this vulnerability. They are targeting SonicWall VPNs to gain initial access to networks and then deploying their ransomware. This group has been observed moving quickly to compromise domain controllers after the initial breach.
Recommended Actions
Given the severity of this threat, organizations using SonicWall VPNs should take the following steps immediately:
- Disable the VPN service: This is the most effective way to prevent exploitation.
- Restrict access via IP allow-listing: If disabling the VPN is not possible, severely restrict access by only allowing connections from trusted IP addresses.
- Monitor network traffic: Look for suspicious activity, such as unusual login attempts or lateral movement.
- Review and update incident response plans: Ensure that your organization is prepared to respond to a ransomware attack.
- Apply available patches: While a zero-day is being exploited, ensure all other available patches are applied.
Key Takeaways
- A zero-day vulnerability in SonicWall VPNs is being actively exploited.
- Attackers are bypassing MFA to deploy ransomware.
- The Akira ransomware group is a major threat actor in these attacks.
- Immediate action is required to mitigate the risk.
References
- Huntress Blog: Active Exploitation of SonicWall VPNs
- TechRadar: SonicWall VPNs are being targeted by a new zero-day
- InfoSec Today: SonicWall Firewall Devices Targeted by Akira Ransomware
- The Hacker News: Akira Ransomware Exploits SonicWall VPNs
- Security Affairs: Akira Ransomware targets SonicWall VPNs
- Truesec: Akira Ransomware Exploiting Potential Zero-Day in SonicWall SSL VPN
- Comparitech: Sonicwall Ransomware Image