Winning the Cyber War: How SOCs Stay Ahead of Emerging Threats
Winning SOCs leverage real-time threat intelligence and proactive monitoring to stay ahead of emerging cyber threats. This allows them to anticipate and neutralize attacks before they impact the organization.
In today's digital landscape, cyber threats are constantly evolving, becoming more sophisticated and harder to detect. Security Operations Centers (SOCs) are the frontline defense against these threats. But what separates a winning SOC from one that's constantly playing catch-up? Let's dive into the strategies and technologies that empower these cybersecurity powerhouses to stay ahead.
Proactive Threat Intelligence: Seeing the Future
Imagine trying to win a race without knowing the course. That's what cybersecurity is like without threat intelligence. Winning SOCs don't just react to attacks; they anticipate them. They leverage threat intelligence feeds, which are constantly updated streams of information about emerging threats, vulnerabilities, and attack patterns. This allows them to proactively identify potential risks and implement preventative measures. Think of it as having a crystal ball that shows you where the next cyberattack might come from.
But it’s not enough to just have the data, it’s about how you use it. Are you actively analyzing threat intelligence to tailor your defenses? Are you using it to simulate potential attacks and test your incident response plans?
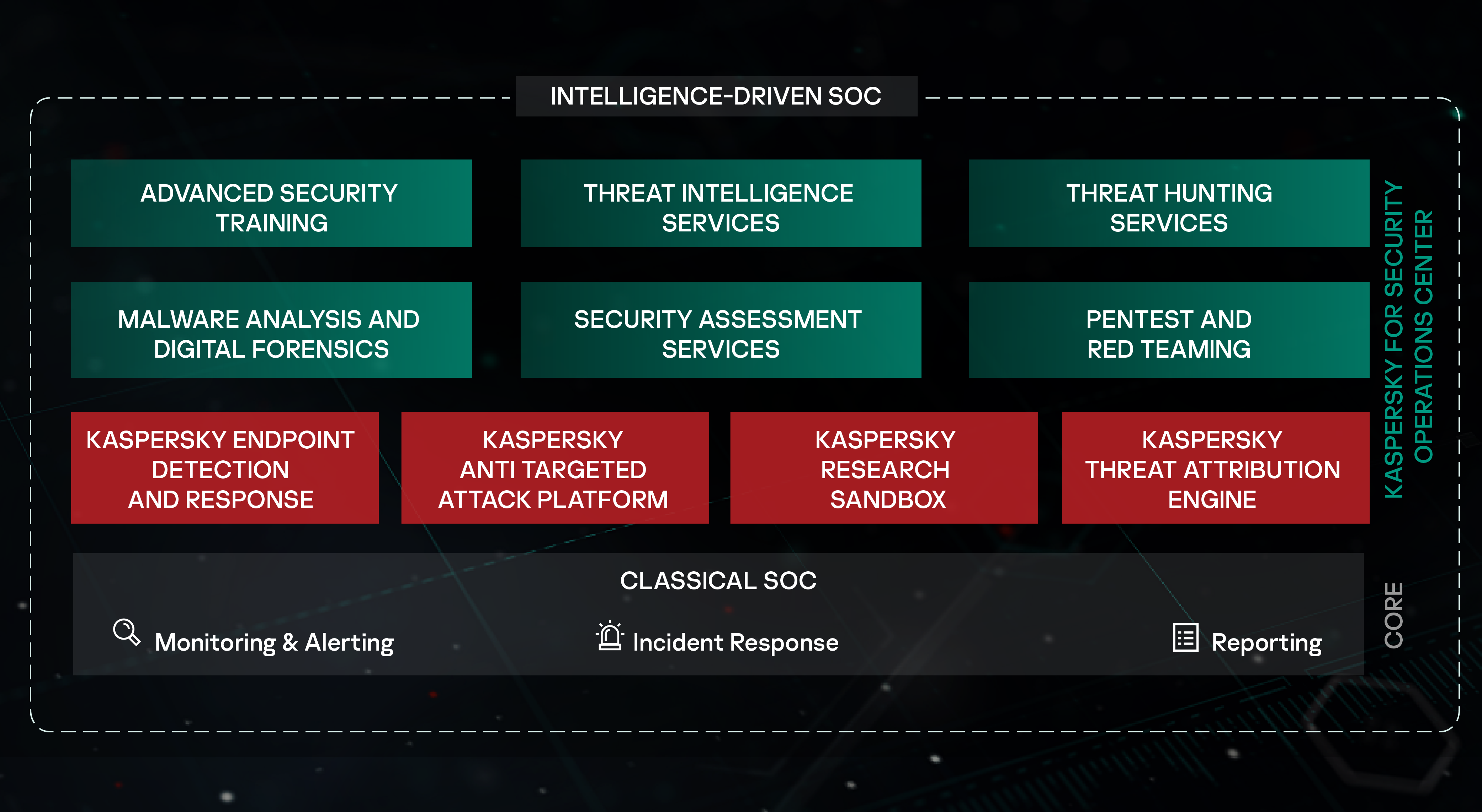
Advanced Security Tools: The Arsenal of Defense
A skilled warrior needs the right tools, and a SOC is no different. Advanced Security Information and Event Management (SIEM) systems are the cornerstone of modern SOCs. SIEMs collect and analyze security data from across the organization, providing a centralized view of potential threats. Endpoint Detection and Response (EDR) solutions add another layer of defense by monitoring individual devices for malicious activity. Other critical tools include intrusion detection/prevention systems (IDS/IPS), vulnerability scanners, and sandboxing environments.
The key is integration. These tools must work together seamlessly to provide comprehensive visibility and coordinated response capabilities. Is your SOC's toolset a well-oiled machine, or a collection of disparate systems?
Automation and Orchestration: Streamlining the Fight
In the fast-paced world of cybersecurity, speed is everything. Automation and orchestration are essential for streamlining SOC operations and reducing response times. Security automation involves using technology to automate repetitive tasks, such as threat detection, incident triage, and vulnerability scanning. Security orchestration takes it a step further by coordinating and automating workflows across multiple security tools and systems. This allows SOC analysts to focus on the most critical threats and respond more effectively.
Consider this: could automation free up your team to focus on more strategic initiatives? Are you maximizing the potential of your security tools through orchestration?
Skilled Personnel and Training: The Human Element
Technology is important, but it's the people who make a SOC truly effective. A team of skilled and experienced security analysts is essential for identifying, investigating, and responding to cyber threats. Continuous training and development are crucial for keeping analysts up-to-date on the latest threats and technologies. Building a strong SOC team also involves fostering a culture of collaboration, knowledge sharing, and continuous improvement.
Are you investing in your team's skills and creating an environment where they can thrive?
Risk Assessment and Compliance: Knowing Your Weaknesses
A winning SOC understands the organization's risk profile and compliance requirements. Regular risk assessments help identify vulnerabilities and prioritize security efforts. Compliance mandates, such as GDPR, HIPAA, and PCI DSS, require organizations to implement specific security controls. A SOC plays a critical role in ensuring that these controls are effectively implemented and maintained.
Do you know where your organization's biggest security gaps are? Are you proactively addressing them?
My Take: The Future of SOCs
I believe the future of SOCs lies in even greater automation, AI-driven threat detection, and proactive threat hunting. The increasing complexity of cyber threats demands a more sophisticated approach to security. SOCs will need to become more agile, adaptive, and proactive in order to stay ahead of the curve. The challenge will be balancing automation with the human element, ensuring that analysts have the skills and knowledge to effectively leverage these advanced technologies.
Here’s the story of winning SOCs. We’ve dove into the challenges they face, the solutions they employ, and what it all means for the future. By now, you should have a better understanding of how SOCs stay ahead of emerging threats and how it impacts you!
References
What is a Security Operations Center ( SOC ) | Zscaler Overview
SOC 2 Compliance: Best Practices - Cybecs
Defending Against Business Email Compromise: SOC Best Practices ...
Incident Response In SOC : Best Practices And How Digi9 Secures...
Strategies for Building a Strong SOC Team and Developing Analysts
