MCP Server Explained: The Protocol Unleashing AI's Potential
MCP Servers: The Hidden Security Risks in AI-Driven Cyber Defense

MCP Server Explained: The Protocol Unleashing AI's Potential
AI is revolutionizing cyber defense, offering unprecedented capabilities in threat detection and response. But like any powerful technology, it comes with its own set of risks. One emerging area of concern is the security of MCP servers. What exactly are they, and why should you be worried? Let's dive in!
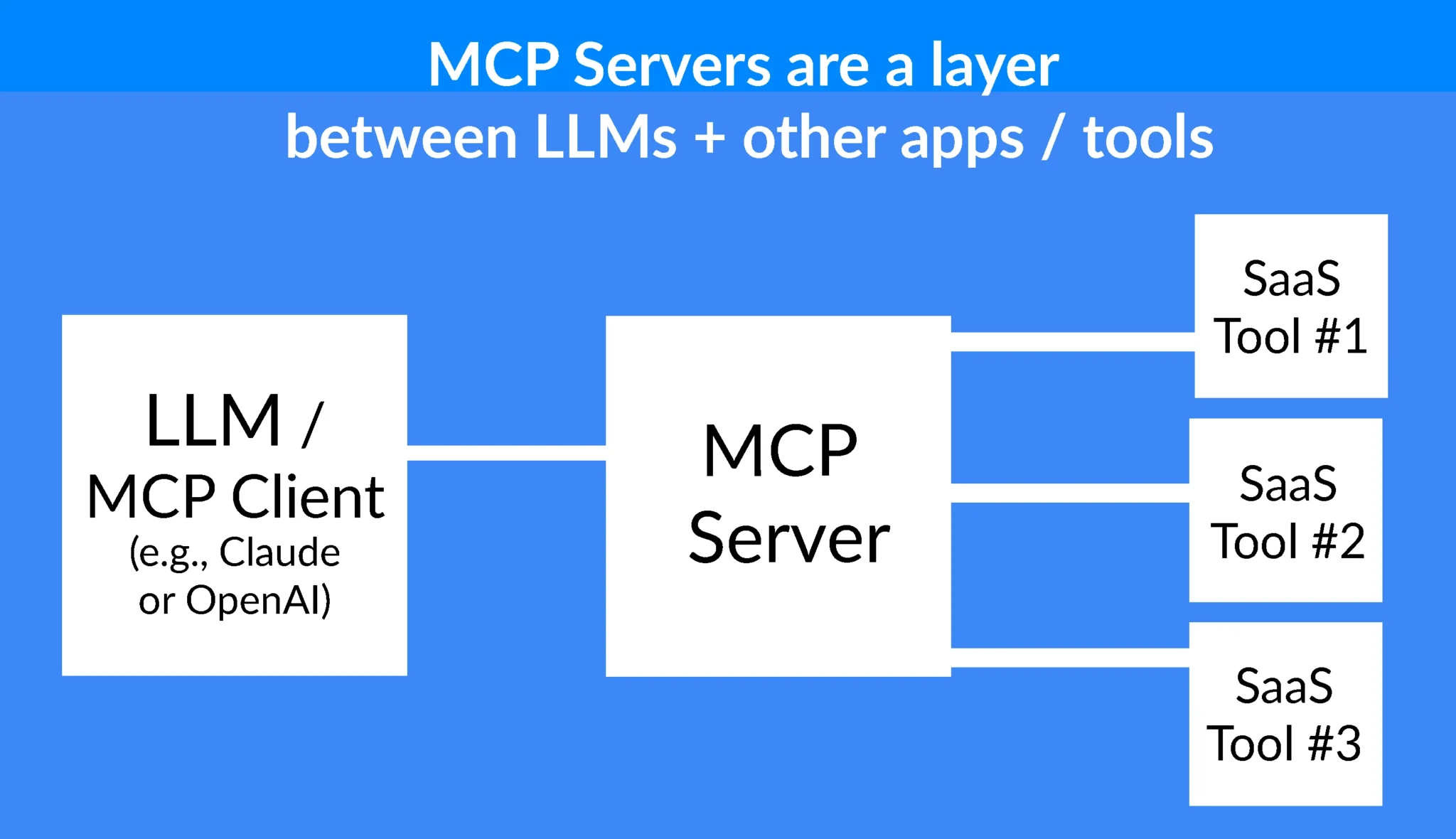
What is an MCP Server?
MCP stands for Model Context Protocol. Think of it as a standardized way for AI agents to talk to different tools, databases, and services. It's like a universal translator that allows AI to access and use information from various sources to make better decisions in cyber defense. Launched in late 2024, it's quickly becoming popular.
Imagine an AI assistant that can investigate security incidents, reconstruct attack timelines, and report on your security posture, all through simple conversational queries. That's the promise of MCP. Vectra AI and Cyware are among the companies offering MCP servers to make this a reality.
The Dark Side: Security Risks
Here's the catch: while MCP offers amazing potential, it also introduces new security vulnerabilities. It's like giving your AI the keys to the kingdom without properly vetting its friends. So, what are the specific risks?
- Hardcoded Credentials: Some MCP servers have been found with hardcoded credentials in their configuration files. It's like leaving your front door unlocked with a welcome mat that says, "Please, come on in!".
- Prompt Injection: This is where malicious actors inject harmful commands into the AI's prompts, tricking it into doing things it shouldn't. Think of it as whispering bad advice into the AI's ear.
- Token Theft: If an MCP server is compromised, attackers can steal authentication tokens, allowing them to impersonate users and access sensitive data.
- Remote Code Execution (RCE): In severe cases, vulnerabilities in MCP servers can allow attackers to execute arbitrary code on the system. This is like giving them full control of your computer.
These vulnerabilities arise because MCP, like REST before it, wasn't initially designed with strong security in mind. As KuppingerCole points out, API security is becoming the core of enterprise cyber defense, and MCP needs to be part of that conversation.
Why Should You Care?
If you're relying on AI for cyber defense, you need to understand the risks associated with MCP servers. Ignoring these vulnerabilities is like building a fortress with a secret back door. It's crucial to implement proper security measures to protect your systems from attack.
Think about it: Are you regularly reviewing the code of third-party MCP servers? Are you scanning for malware? Are you ensuring that your AI agents have the appropriate permissions? If not, you could be leaving yourself vulnerable.
My Take
MCP has the potential to significantly enhance AI-driven cyber defense, but it's not a silver bullet. The rapid adoption of this technology without sufficient attention to security is concerning. We need to prioritize security best practices and develop robust defenses against these new attack vectors. The future of AI in cyber defense depends on our ability to address these challenges proactively.
As AI continues to evolve, so will the threats against it. Staying informed and vigilant is the best way to protect your systems and data.
References
- MCP Server Explained: The Protocol Unleashing AI's Potential (Image Source)
- Why API Security Is Becoming the Core of Enterprise Cyber Defense
- Beware of MCP Hardcoded Credentials: A Perfect Target for Threat Actors
- MCP Vulnerabilities Every Developer Should Know
- MCP Security - 5 common security vulnerabilities
- MCP Explained: Meaning & Uses
