ClickFix: How Fake Google Meet Errors Install Malware on Your Devices
Microsoft warns users of the ClickFix technique, where hackers use fake Google Meet alerts to install malware on Windows and macOS devices. Stay vigilant and avoid clicking on suspicious links or attachments.
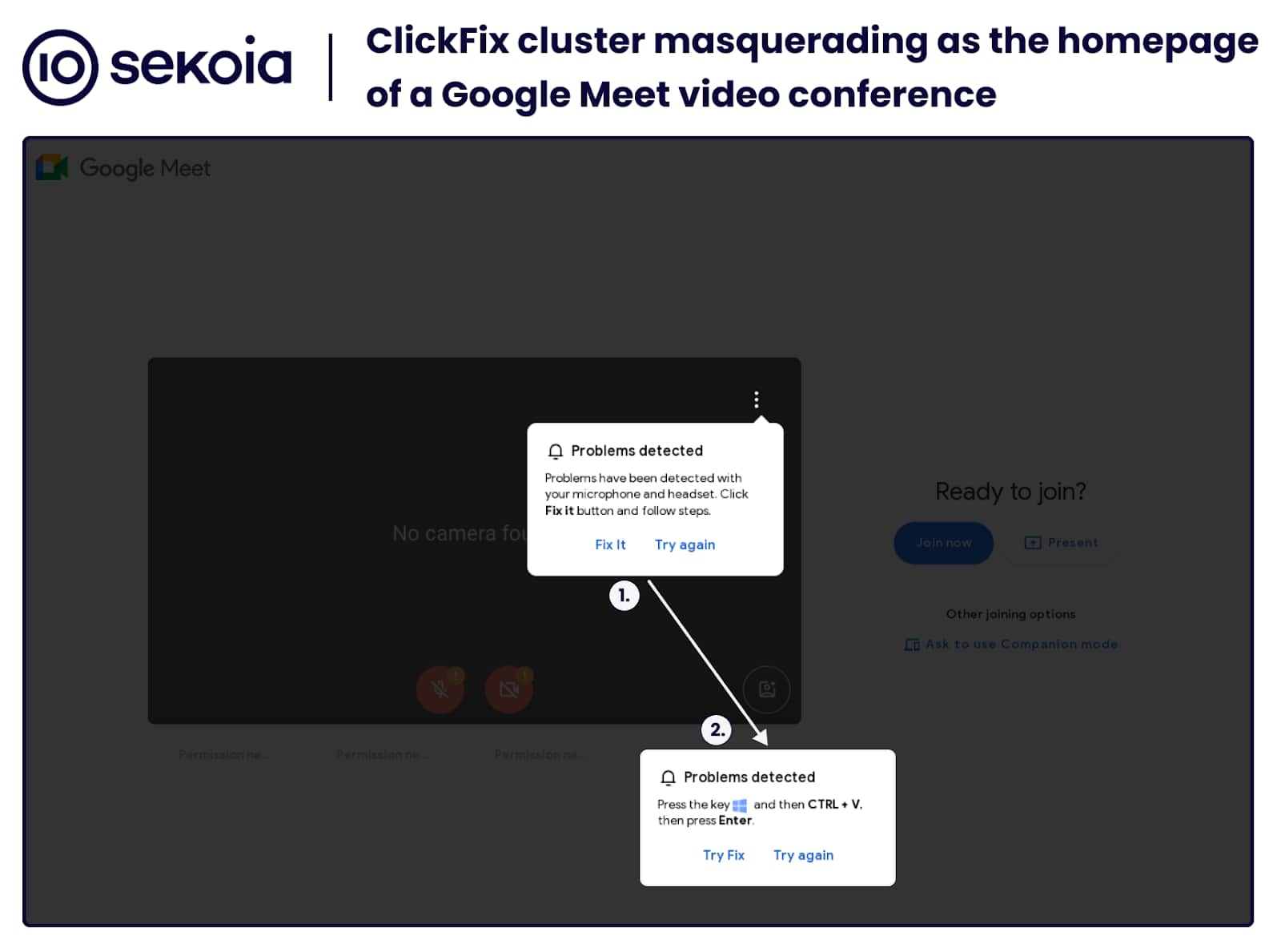
Ever received a Google Meet invite that seemed a little…off? Maybe it led to a page with a weird error message, urging you to "fix" something? If so, you might have encountered the ClickFix technique, a sneaky way hackers are using fake Google Meet alerts to install malware on your computer. Let's dive into what ClickFix is and how you can protect yourself.
What is ClickFix?
ClickFix is a social engineering technique where hackers trick you into running malicious commands by exploiting your desire to fix technical issues quickly. Imagine clicking on a Google Meet link and instead of joining a meeting, you see an error message. The page might suggest you need to update a plugin or run a script to resolve the problem. But here's the catch: that "fix" is actually malware.
These fake Google Meet pages are designed to look legitimate, often mimicking the real Google Meet interface. The error messages are crafted to create a sense of urgency, prompting you to take immediate action without thinking twice. Have you ever been in a rush and just clicked "OK" without reading the fine print? Hackers are counting on that!
The Malware Payload: Info-Stealers and More
So, what kind of nasties are delivered through ClickFix? According to Microsoft security analysts, the payloads can include a variety of malware, with a focus on info-stealers. These are malicious programs designed to steal your sensitive information, such as:
- Passwords: Login credentials for your email, social media, banking, and other accounts.
- Credit card details: Saved credit card numbers and security codes.
- Browser data: Cookies, browsing history, and autofill data.
- Cryptocurrency wallets: Private keys and wallet information.
One of the most prevalent info-stealers distributed through ClickFix is Lumma Stealer. But that's not all. Hackers are also using ClickFix to deliver remote access tools (RATs) like Xworm and AsyncRAT, loaders like Latrodectus and MintsLoader, and even sophisticated rootkits like a modified version of the open-source r77.
How to Protect Yourself from ClickFix
The good news is that you can defend yourself against ClickFix and similar social engineering attacks. Here are some practical steps to take:
- Be skeptical: Always double-check the URL of any Google Meet page you visit. Make sure it's the official Google Meet domain.
- Verify before you click: Never click on links or run scripts from unknown or suspicious sources. If you see an error message, don't blindly follow the instructions on the page.
- Keep your software up to date: Regularly update your operating system, web browser, and antivirus software.
- Use a password manager: A password manager can help you create and store strong, unique passwords for all your accounts, reducing the risk of password theft.
- Enable multi-factor authentication (MFA): MFA adds an extra layer of security to your accounts, requiring you to provide a second form of verification (e.g., a code from your phone) in addition to your password.
My Take
In today's digital landscape, staying informed and vigilant is crucial. The ClickFix technique is a reminder that hackers are constantly evolving their tactics to exploit our trust and curiosity. It's easy to fall victim to these scams, especially when we're in a hurry or distracted. By taking a few extra seconds to verify the legitimacy of a website or link, we can significantly reduce our risk of falling prey to malware and data theft. Let's make cybersecurity awareness a habit, not just an afterthought.
